PANDA’s Threat Goes On Sale For $3000
A new MacOS stealer has surfaced on the dark web, causing concern among cybersecurity experts. Operating under a mysterious name, this information stealer has caught the attention of the security community with its advanced features and capabilities.
Priced at $3000 per month, the MacOS stealer is a sophisticated tool designed to collect sensitive information, posing a significant threat to Mac users.
The Features of the MacOS Stealer
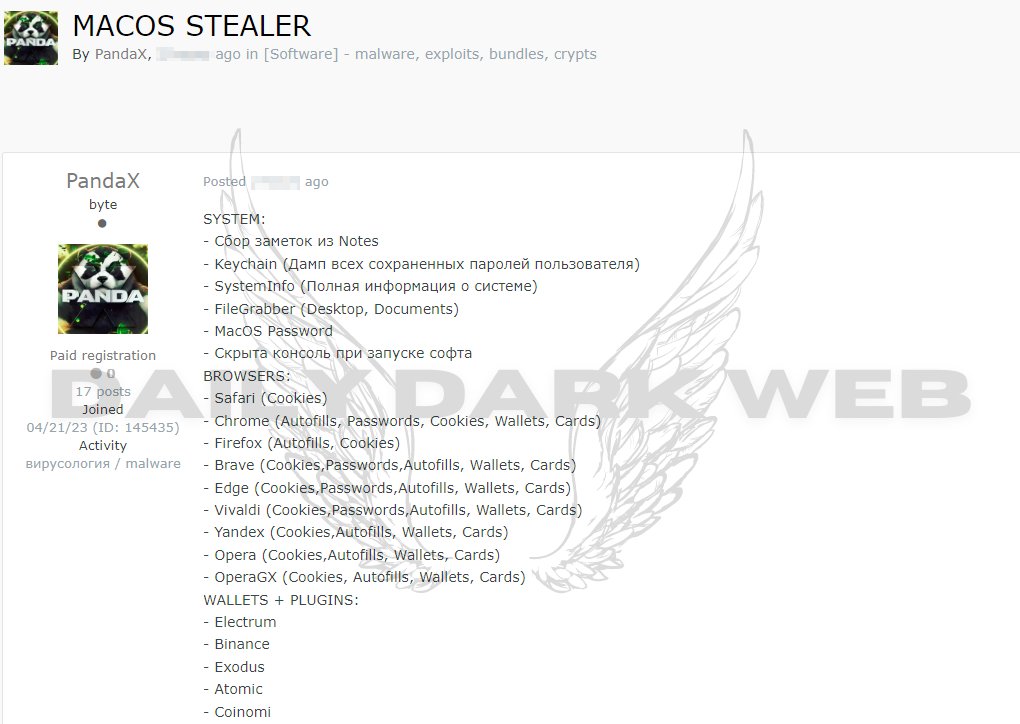
The MacOS stealer, attributed to the PANDA threat actor and known as PandaX, boasts an array of powerful features. The threat actor’s post outlines its ability to collect notes, keychain dumps, system Information, and MacOS passwords, and employ features such as FileGrabber and a hidden console during software initiation. This comprehensive range of functionalities enables the stealer to access and compromise various aspects of a user’s system.
Notably, the MacOS stealer is not limited to a specific browser or platform. It is designed to infiltrate popular browsers like Safari, Chrome, Firefox, Brave, Edge, Vivaldi, Yandex, Opera, and OperaGX. Its capability to target a wide range of browsers makes it a versatile threat, posing risks to users across different online environments.
MacOS Information Stealer: Wallets and Plugins
The MacOS stealer doesn’t stop at browser data; it also targets cryptocurrency wallets and plugins. With the ability to compromise wallets such as Electrum, Binance, Exodus, Atomic, and Coinomi, the stealer poses a significant risk to individuals involved in cryptocurrency transactions.
This is not the first time a MacOS information stealer has emerged. Cybersecurity researchers recently identified an upgraded version of a MacOS information stealer named Atomic. The active enhancement of such malware indicates a continuous effort by threat actors to stay ahead of security measures.
The MacOS stealer follows a similar modus operandi to its predecessors. The threat actors often repackage pre-cracked applications as PKG files, embedding a Trojan proxy and a post-install script to initiate the infection.
Users are deceived into installing compromised applications, leading to the stealthy infiltration of their systems. The recent emergence of the MacOS information stealer by multiple threat actors highlights the adaptability and persistence of threat actors.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
